|
<< Click to Display Table of Contents >> Standard single sign-on |
|
|
<< Click to Display Table of Contents >> Standard single sign-on |
|
❖Realization mode
Yonghong supports single sign-on using token authentication, which is described in detail below.
❖Token Verification principle description
After logging in to their own system, the customer hopes to open Yonghong's report or function module directly, but this user may not have been created in Yonghong system before. This approach requires that the token parameter and the sysFlag parameter be included after the url of the report or function module (sysFlag is not necessary, which is used to distinguish the callback interfaces of multiple system token validations, and to select different callback addresses depending on the parameters. If there is no parameter or if the parameter is an empty string, the default configured url callback interface is read), when the report or module's ur is clicked L, the Yonghong system intercepts these requests, invokes the callback interface provided by the client system (which requires customer development) to verify that the token is generated legally, and returns the current user information through the post-callback interface. Yonghong system will determine whether the current user already exists, if not, it will create the user and log on to the system directly after it has been created, so as to avoid the appearance of the login page.
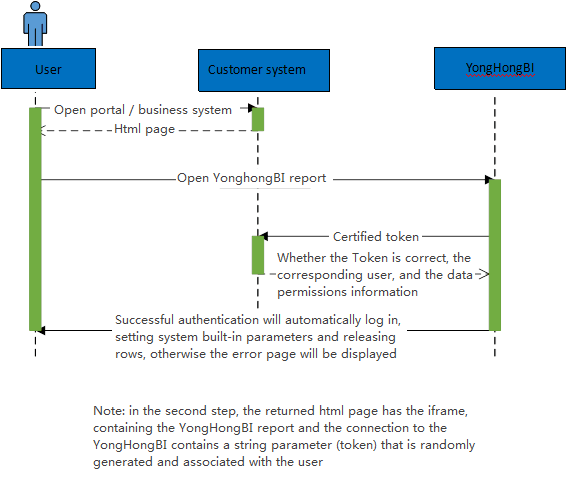
The Token and callback interfaces are generated by the customer system for the following reasons:
When the user enters the Yonghong system from the client system, it may not exist in the Yonghong system. At this time, Yonghong needs to obtain the current user information from the customer system and automatically create it in the Yonghong system to access the Yonghong system. Using token instead of passing the user name directly is for security reasons and needs to be verified first.
The Token and callback interfaces need to meet the following conditions:
According to the current session generation of the current logged-in user, each time is different, hash algorithm or other algorithms can be used.
Customers need to develop interfaces to verify the Yonghong backhaul interface, and to return the current login user-related information based on the token.
❖Token callback usin
Token callback Interface description
Request address |
callback.url |
Request parameter (Post mode) |
token: E2ABA91383139F9D4B4D7C1E0226FA1B |
Return parameter |
{ "result": "success", "userId": "john", "userAlias": "john", "userEmail": "john@.com", "userRoles": "role1,role2", "userGroups": "group1/subgroup1,group2/subgroup2", "param":{ "department": "general headquarters", "city": "beijing", "xxx": "xxx" } } |
➢Note:
Callback validates the token interface, which can be validated by post, with the parameter name token
Callback validation token interface validation succeeded, returned results must have the values of result and userId. Result for interface callback success, if the other value returned is failed .UserID is the user name in Yonghong. UserAlias optional, is the user alias .useremail optional. Is a user mailbox .userRoles optional, is a user role, if a user has multiple roles that are comma separated .userGroups optional, is a user group, and if the user belongs to multiple groups separated by a comma, write to the group Param is optional, corresponding to a json object that stores the data that needs to be placed in the built-in parameters of the product, which can be used for data permission filtering.
Token delivery mode
Token can be placed behind the url or submitted via post or in header. Put it at the back of the url, for example:
http://localhost:8080/bi/Viewer?proc=1&action=viewer&token=E2ABA91383139F9D4B4D7C1E0226FA1B
Example of the customer's callback interface java code
(can not be used directly, requires customer improvement)
package com.customer.service;
import java.io.IOException;
import javax.servlet.ServletException;
import javax.servlet.http.*;
public class TokenCheckServlet extends HttpServlet {
private static final long serialVersionUID = 1L;
public TokenCheckServlet() {
super();
}
protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
String token = request.getParameter("token");
if(token == null || "".equals(token.trim())) {
// Customer's own error handling logic
return;
}
else {
// Verify that token is legal
StringBuilder responseStr = new StringBuilder();
if(check(token)) {
//Token authentication returns the current logged-in user through the. Corresponds to users in Yonghong system
responseStr.append("{\"result\":\"success\",\"userId\":\"test\"}");
}
else {
//Failure of token validation to return userId.
responseStr.append("{\"error\":\"james\"}");
}
response.getWriter().write(responseStr.toString());
}
}
private boolean check(String token) {
return true;
}
protected void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
doGet(request, response);
}
}