|
<< Click to Display Table of Contents >> Security Configuration |
|
|
<< Click to Display Table of Contents >> Security Configuration |
|
Description: Yonghong Desktop does not support security configuration.
The security management system is used to set user's permission for accessing the system. For example, a certain user can only login into the user portal interface to access the existing dashboard, and cannot edit the dashboard by logging into the editor dashboard or other interface. Security management system is divided into four categories: no security system, file system security, LDAP synchronization & file system security and customized security.
❖No Security System
When the user selects this item, the authentication and authorization interface on the interface is not displayed, as shown in the following figure:
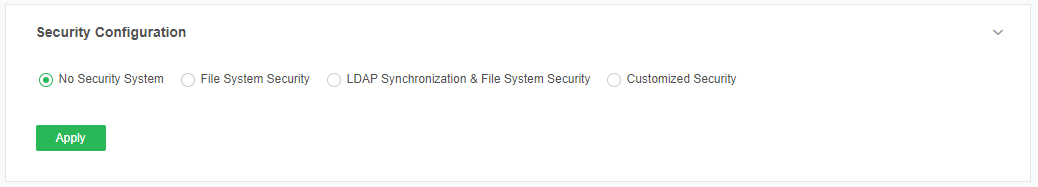
Anyone of this product can enter the modules of Create Connection, Create Data Set, Advanced Analytics, Create Dashboard, View Dashboard and Schedule Tasks, but only administrators can access the Manage System. When Anyone switches from the other module to the "Manage System" module, a prompt will pop up on the current page, as shown in the following figure:
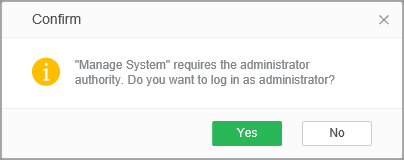
Click "Yes" to enter the administrator login interface, as shown below:
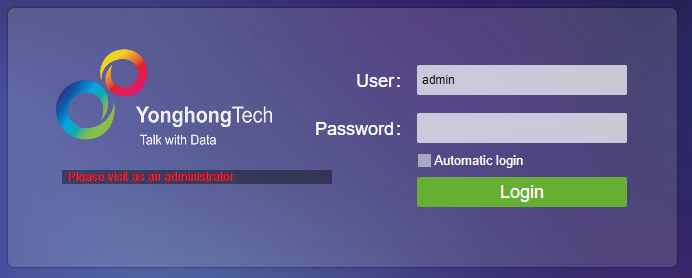
After login, you can enter the management system. Click "No" to stay in the original interface.
❖File System Security
The file permission management system is a management system provided by this product, and the authorization class and authentication class are all default, and the user cannot modify it. When this option is selected, the Authorize Users module on the interface is available as shown in the following figure:
After the user selects the file system security, the user must enter a username and password when accessing any module of the product.
❖LDAP Synchronization & File System Security
When the user selects this type of permission management system, the LDAP configuration module is displayed in the secondary navigation bar of the Authorize Users interface. The user can connect to the LDAP server by configuring the mapping relationship between the LDAP server and the permission system. You can synchronize the users in LDAP into the system through this type, and give resources and actions permissions to users, as shown in the following figure:
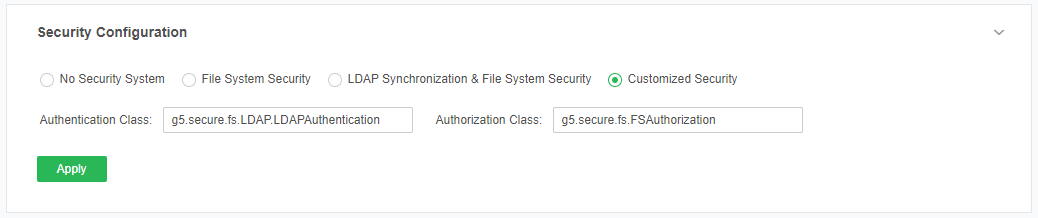
❖Customized Security
When the user choose this type of permission management system, they need to use user-defined authorization class and authentication class. The default authorization class and authentication class displayed is the class of the previously selected permission management system, as shown in the following figure: